HUFUCTF-REVER-toplay
0x1 分析java层
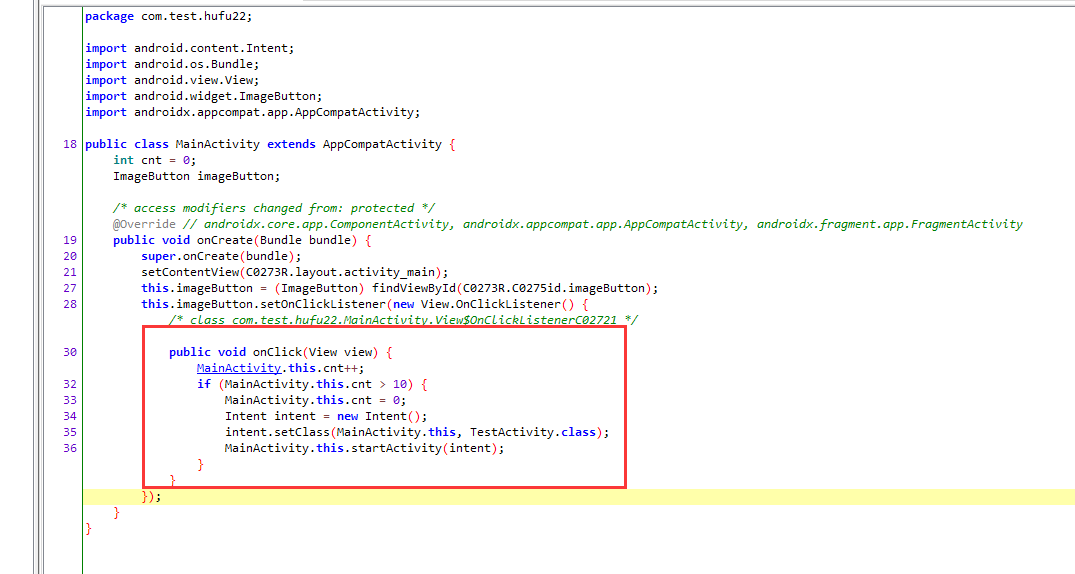
点击一片区域10次触发
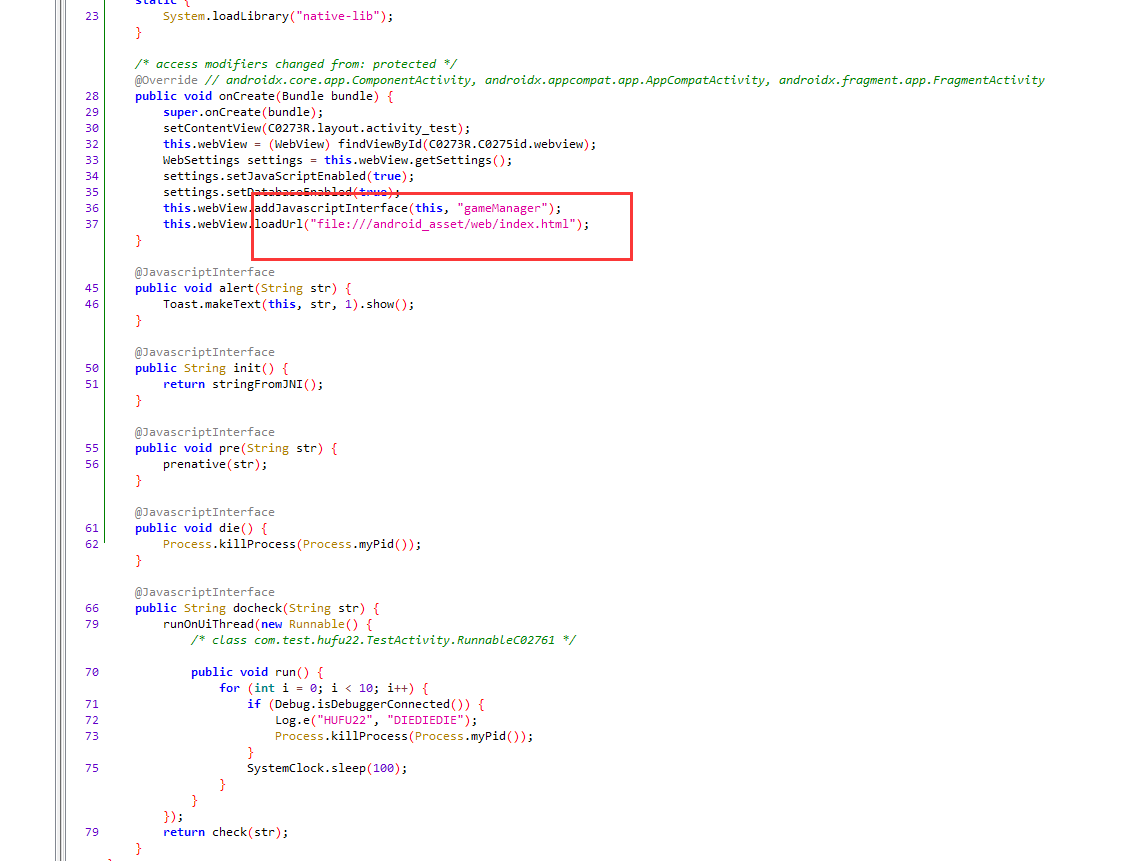
一个网页,进去就是2048游戏
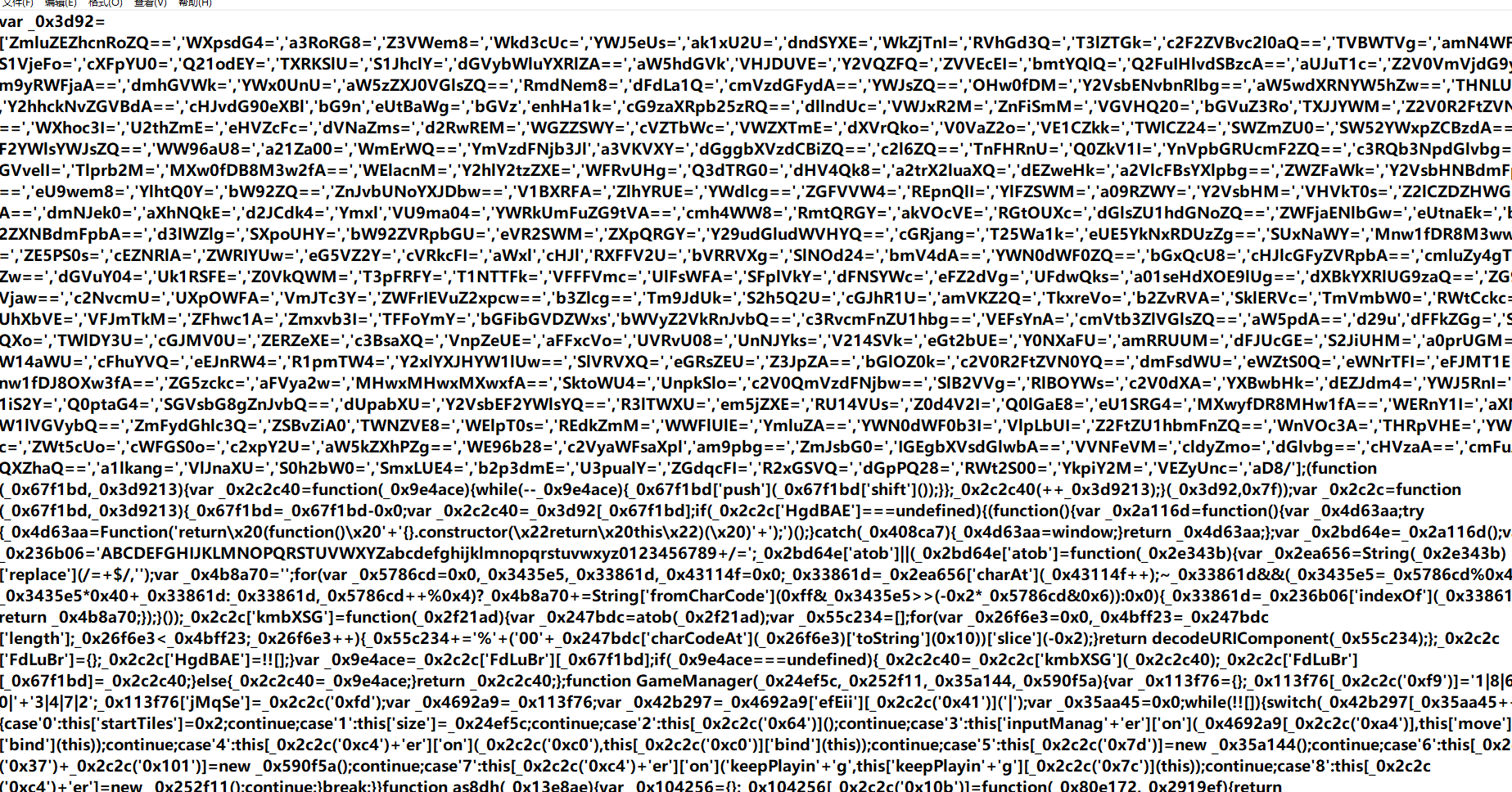
发现经过了base混淆
http://www.dejs.vip/encry_decry/obfuscator.html
http://tool.yuanrenxue.com/decode_obfuscator
解混淆,各位老爷里面请
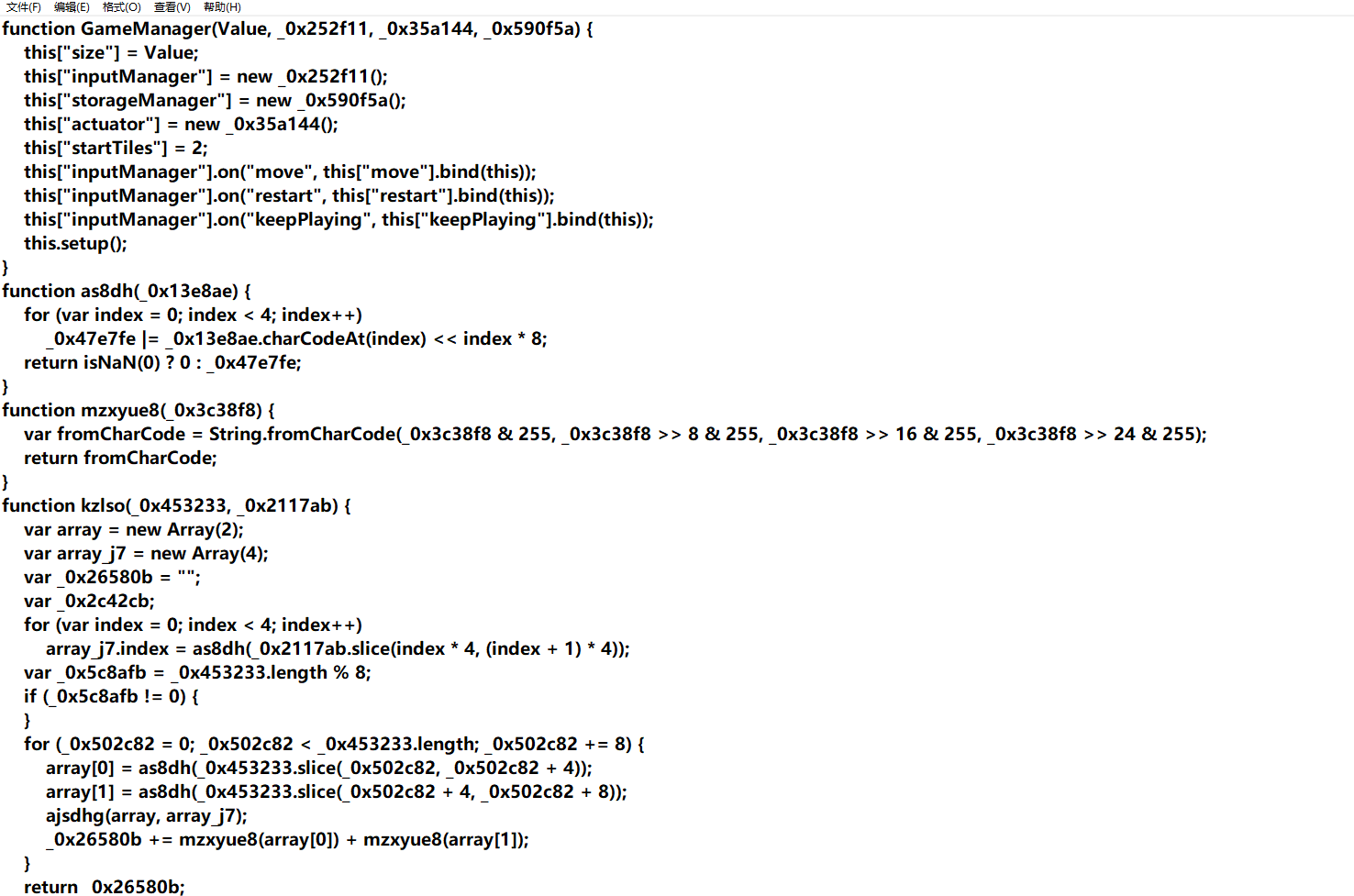
0x2 分析so层
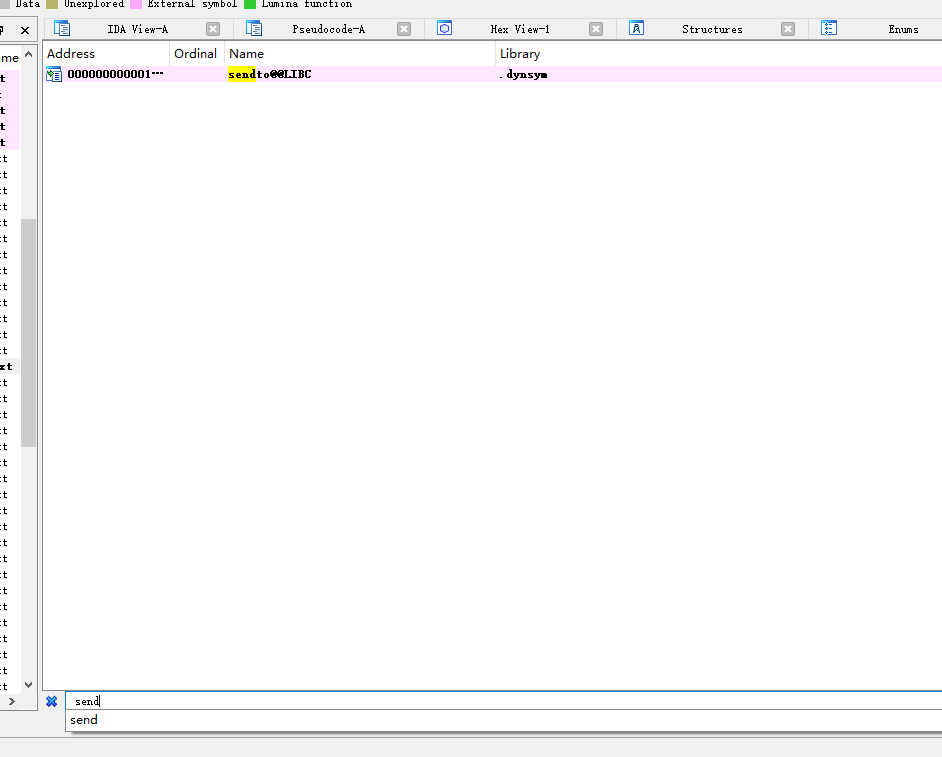
思路是要发送流量包出来,所以搜send函数
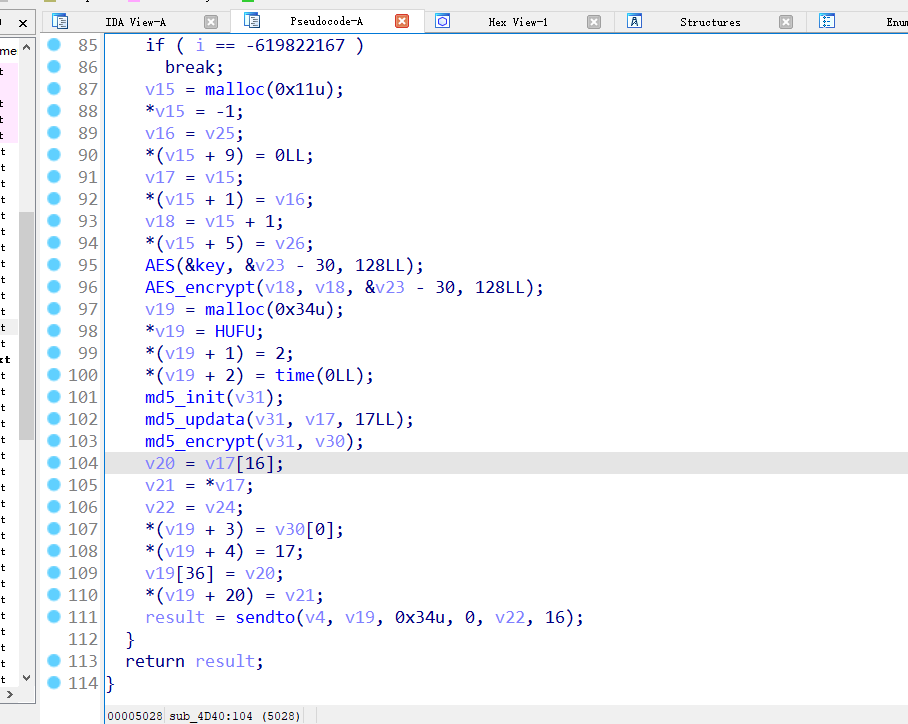
找到关键调用位置,里面改名怎么判断,aes看加密过程和sbox盒,md5_init里面有md5幻值
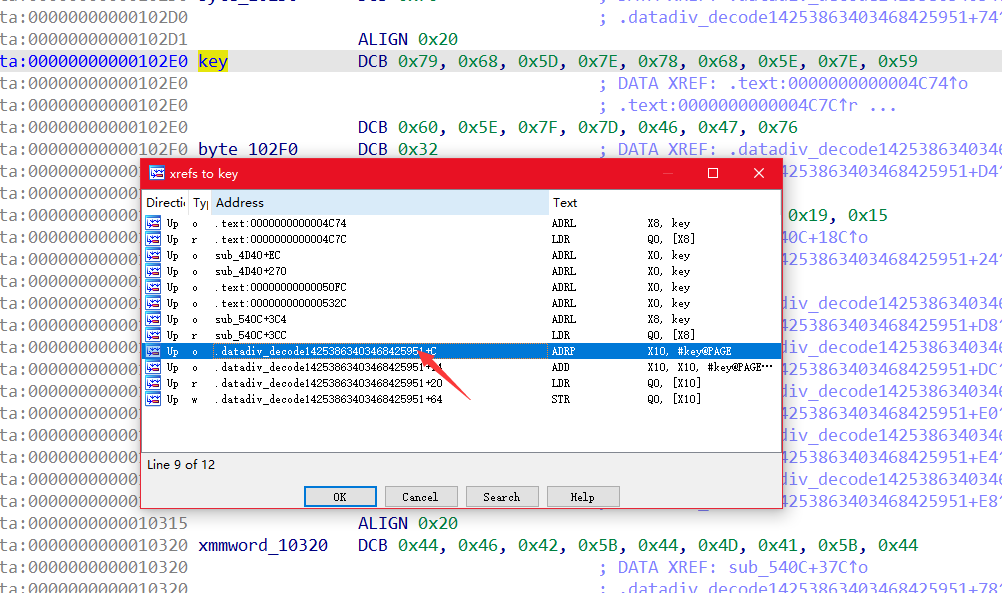
aes密钥查看引用
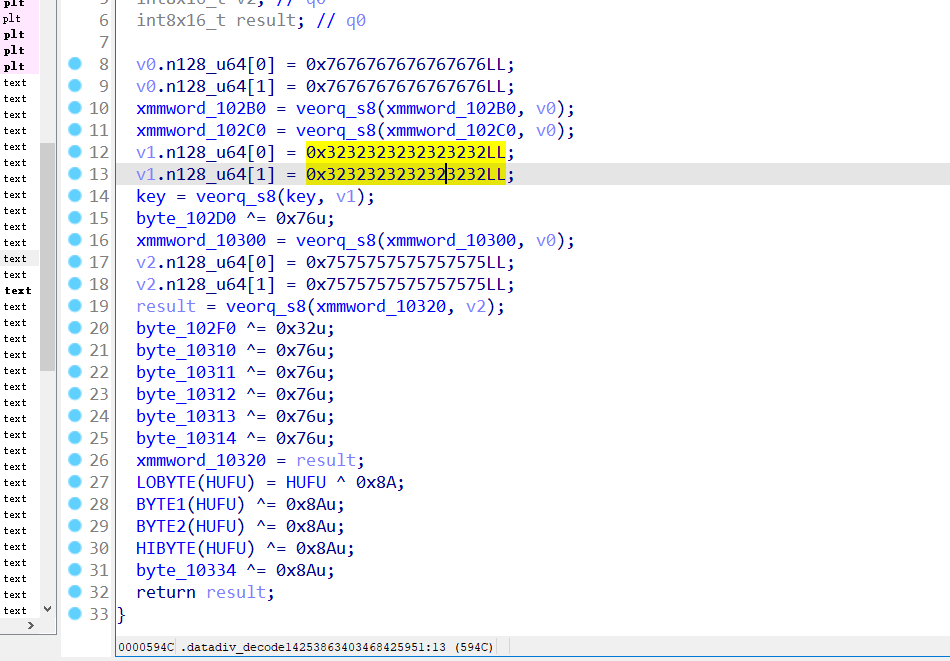
有字符串加密
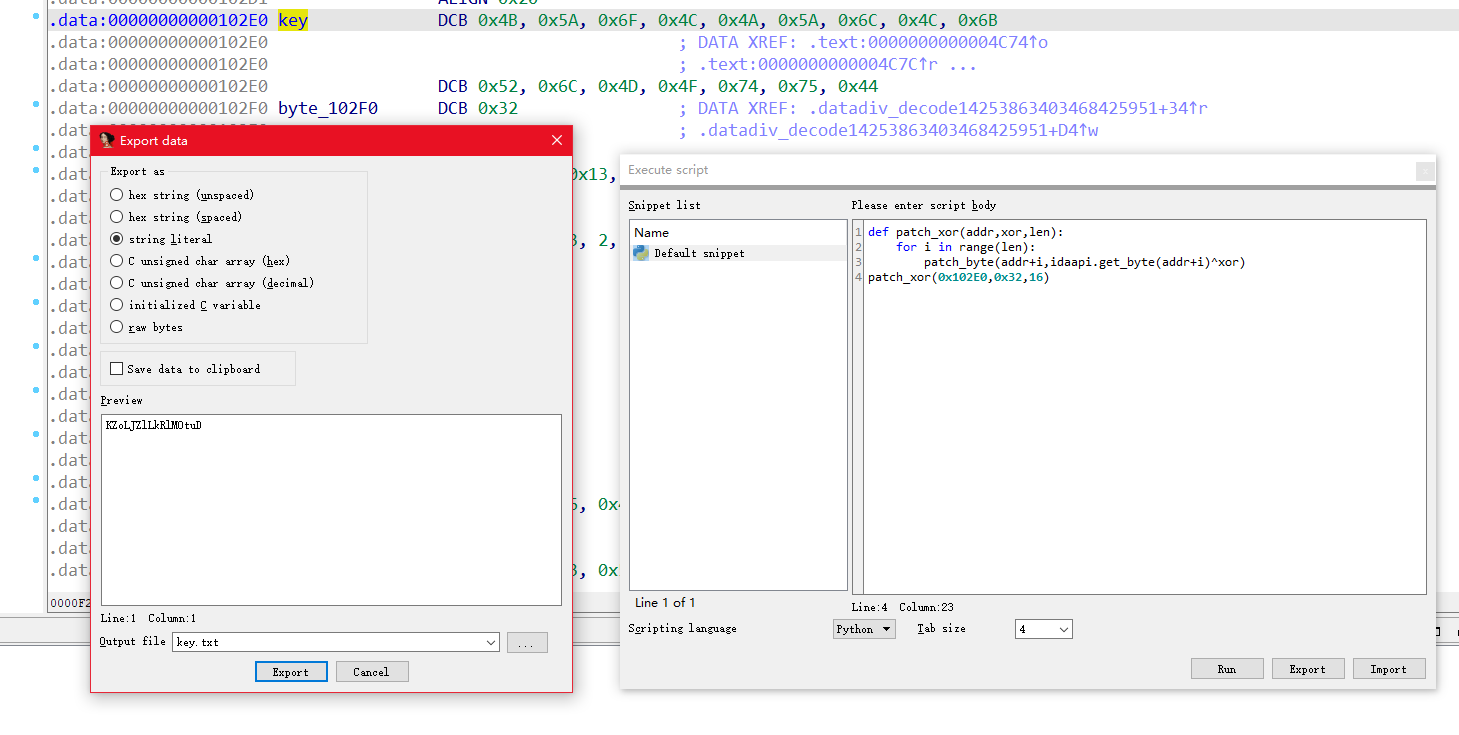
解密回去得到key
0x3 查看流量包
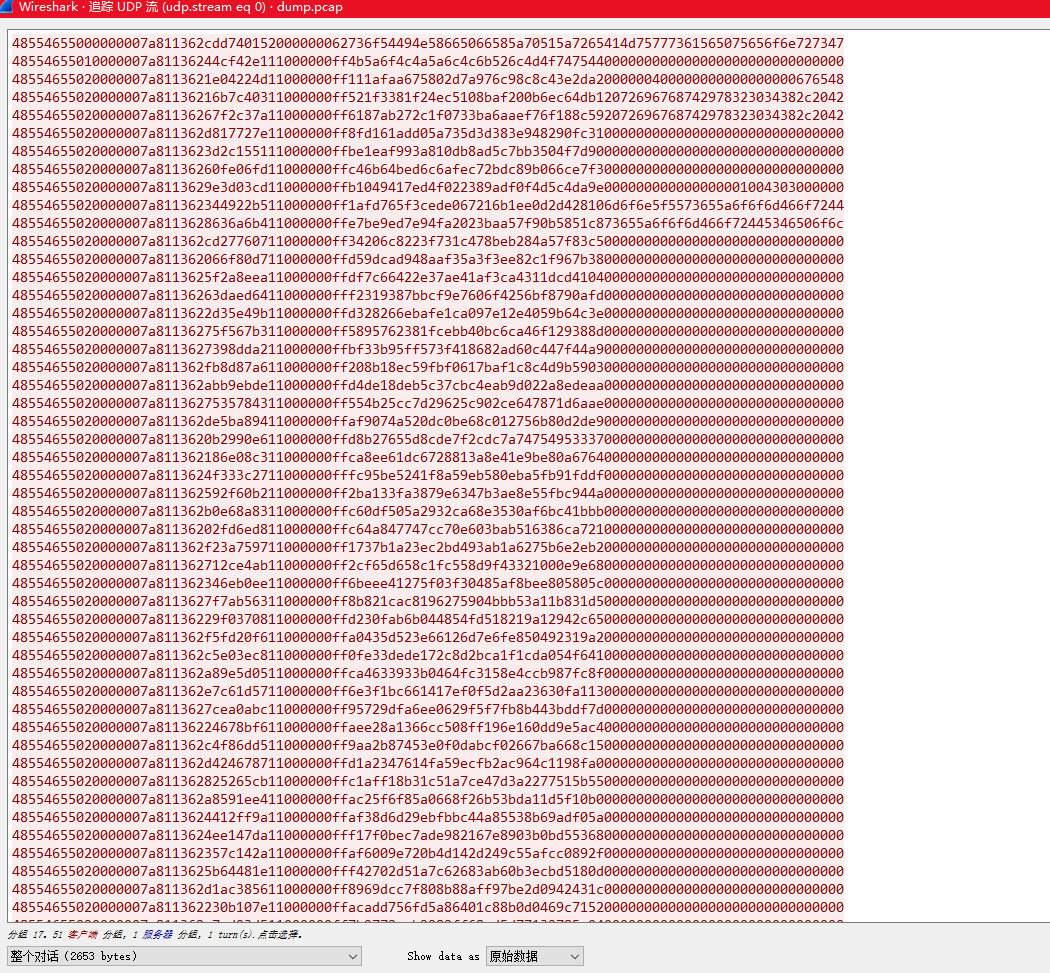
把aes的加密数据提取出来解密
0x4解密AES
from Crypto.Cipher import AES
import binascii
key=b"KZoLJZlLkRlMOtuD"
aes = AES.new(key,mode=AES.MODE_ECB)
data='''
111afaa675802d7a976c98c8c43e2da2
521f3381f24ec5108baf200b6ec64db1
6187ab272c1f0733ba6aaef76f188c59
8fd161add05a735d3d383e948290fc31
be1eaf993a810db8ad5c7bb3504f7d90
c46b64bed6c6afec72bdc89b066ce7f3
b1049417ed4f022389adf0f4d5c4da9e
1afd765f3cede067216b1ee0d2d42810
e7be9ed7e94fa2023baa57f90b5851c8
34206c8223f731c478beb284a57f83c5
d59dcad948aaf35a3f3ee82c1f967b38
df7c66422e37ae41af3ca4311dcd4104
f2319387bbcf9e7606f4256bf8790afd
d328266ebafe1ca097e12e4059b64c3e
5895762381fcebb40bc6ca46f129388d
bf33b95ff573f418682ad60c447f44a9
208b18ec59fbf0617baf1c8c4d9b5903
d4de18deb5c37cbc4eab9d022a8edeaa
554b25cc7d29625c902ce647871d6aae
af9074a520dc0be68c012756b80d2de9
d8b27655d8cde7f2cdc7a74754953337
ca8ee61dc6728813a8e41e9be80a6764
fc95be5241f8a59eb580eba5fb91fddf
2ba133fa3879e6347b3ae8e55fbc944a
c60df505a2932ca68e3530af6bc41bbb
c64a847747cc70e603bab516386ca721
1737b1a23ec2bd493ab1a6275b6e2eb2
2cf65d658c1fc558d9f43321000e9e68
6beee41275f03f30485af8bee805805c
8b821cac8196275904bbb53a11b831d5
d230fab6b044854fd518219a12942c65
a0435d523e66126d7e6fe850492319a2
0fe33dede172c8d2bca1f1cda054f641
ca4633933b0464fc3158e4ccb987fc8f
6e3f1bc661417ef0f5d2aa23630fa113
95729dfa6ee0629f5f7fb8b443bddf7d
aee28a1366cc508ff196e160dd9e5ac4
9aa2b87453e0f0dabcf02667ba668c15
d1a2347614fa59ecfb2ac964c1198fa0
c1aff18b31c51a7ce47d3a2277515b55
ac25f6f85a0668f26b53bda11d5f10b0
af38d6d29ebfbbc44a85538b69adf05a
f17f0bec7ade982167e8903b0bd55368
af6009e720b4d142d249c55afcc0892f
f42702d51a7c62683ab60b3ecbd5180d
8969dcc7f808b88aff97be2d0942431c
acadd756fd5a86401c88b0d0469c7152
7b9772ccb2282ff68ed5d77132785c04
'''.split()
enc = []
for i in data:
enc.append(aes.decrypt(binascii.a2b_hex(i))[4])
print(enc)0x5 继续分析so层
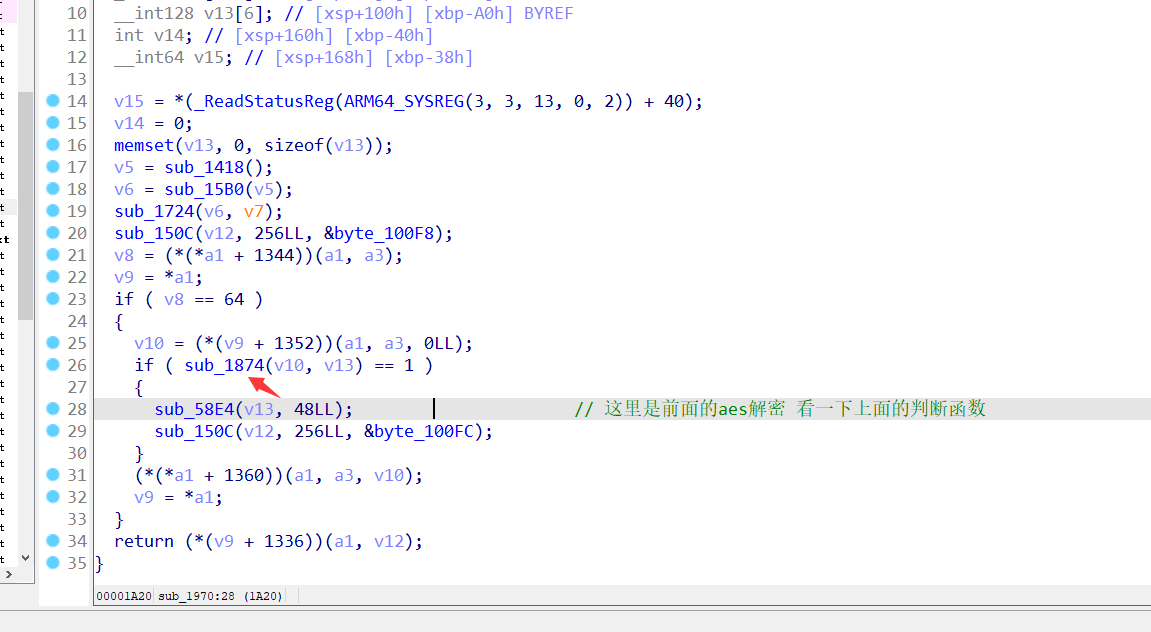
从58E4函数出来外部有一个判断
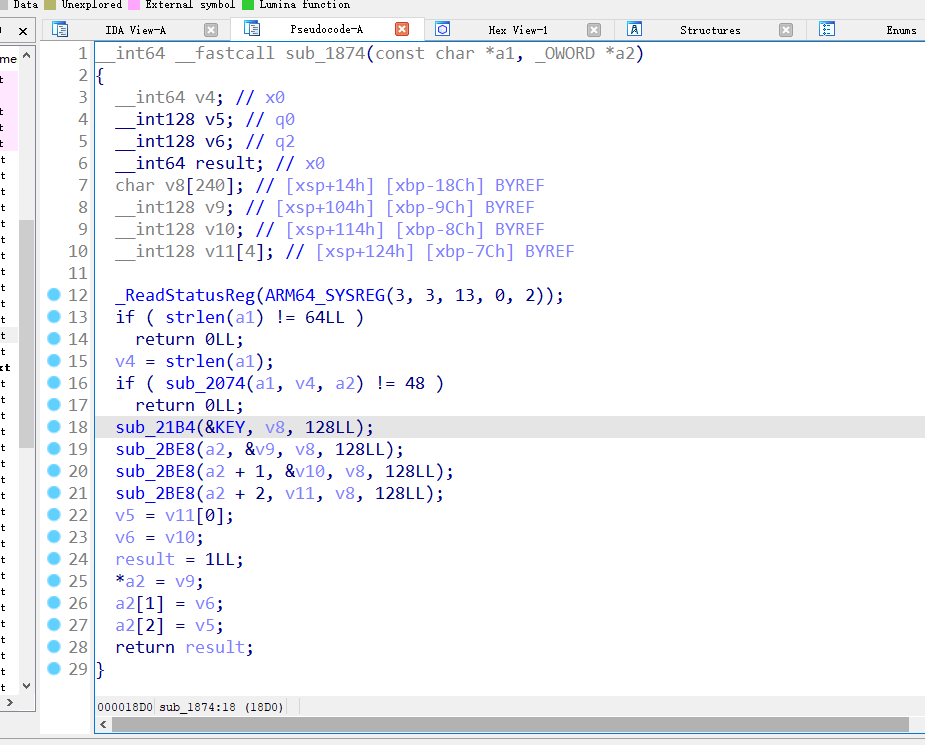
又是一个aes加密
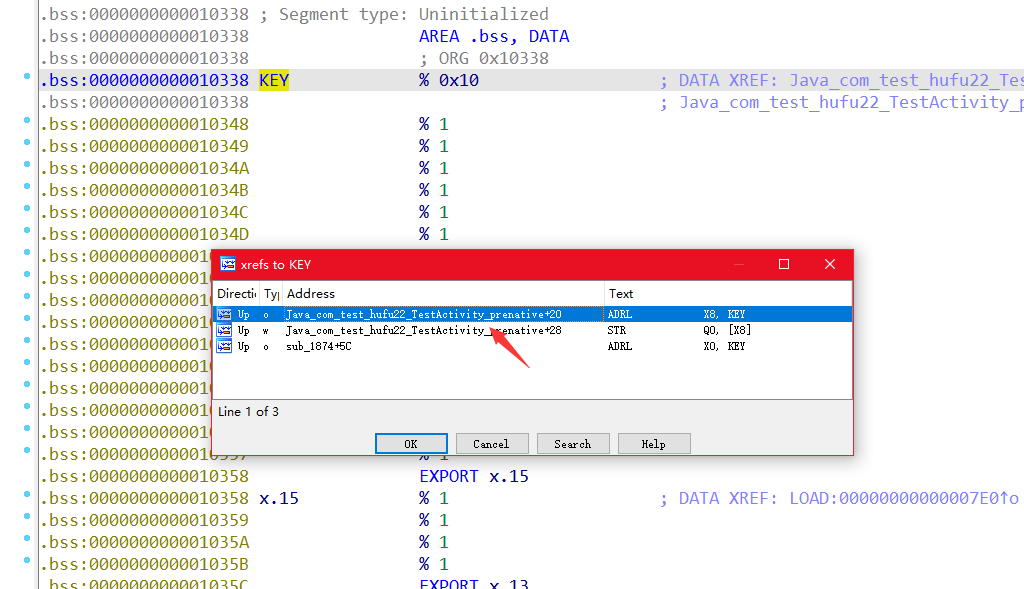
字符串莫得,查看一下引用
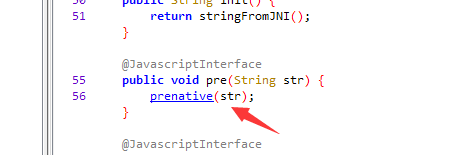
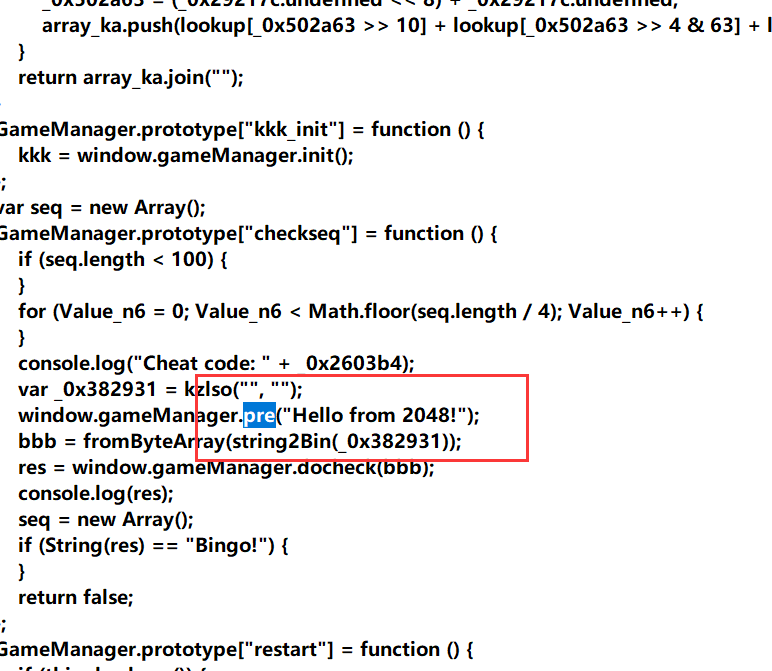
得到aes密钥,解密aes
0x6分析js文件里的xtea加密
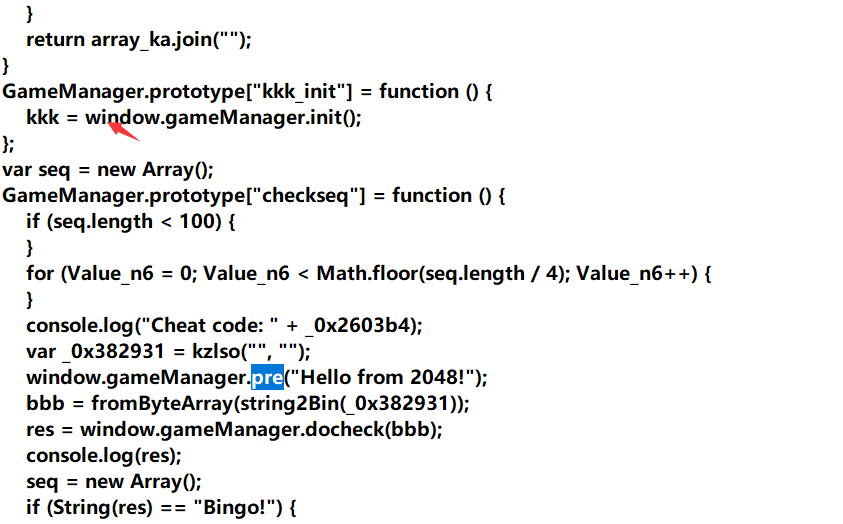
这里的kkk是xtea密钥
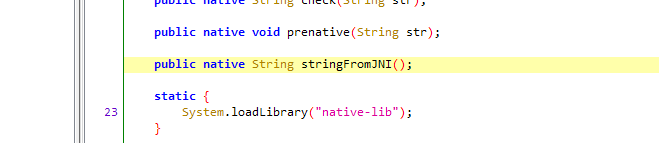
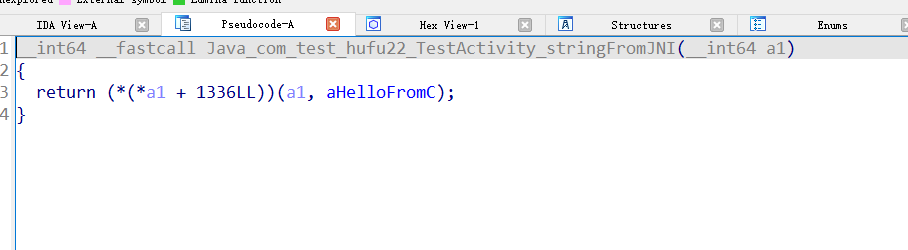
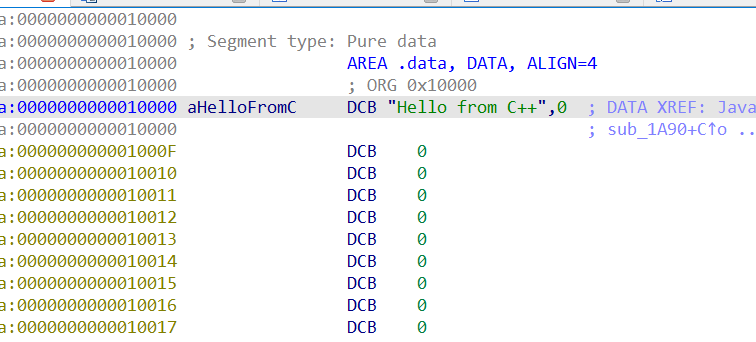
但是这里的密钥不是真的,需要动调so获得(这里有一个反调试,那就是小米和魅族不支持webview,我的手机刚好是小米,无法动调so)我点了
f = '(up, up, down, down, left right, left right)x2048, B, A, Start'
m = 0
key = []
for i in range(16):
print(f[i])
m |= (ord(f[i]) << ((i%4) * 8))
print(m)
if ((i+1)%4) == 0:
key.append(m)
m = 0
print(key)给大家来一份真正的密钥,战队师傅博客(上篇文章那个)偷的。
0x7 总结
学习了碰到流量包和apk怎么分析和思路
然后又是各种解密,aes还换了sbox,很烦。



