HUFUCTF2022-REVER-shellcode
0x0 前言
承接上文的tmd脱壳,所以直接来到ida分析环节
0x1 IDA分析
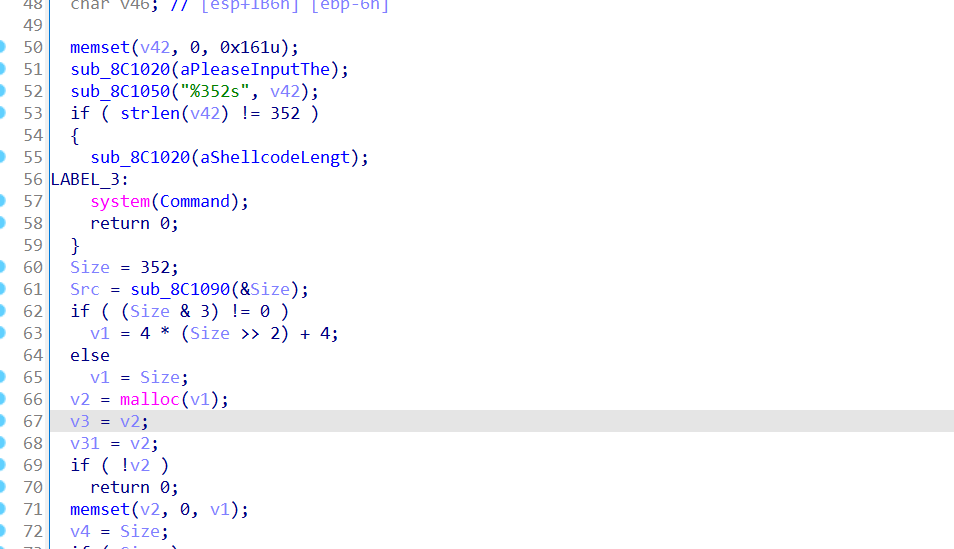
要求输入352位
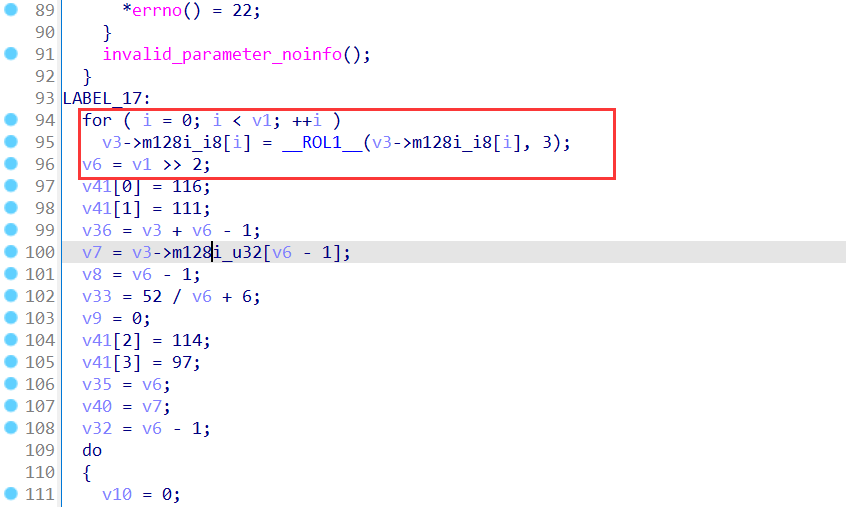
会对每一位进行一个逻辑左移3位
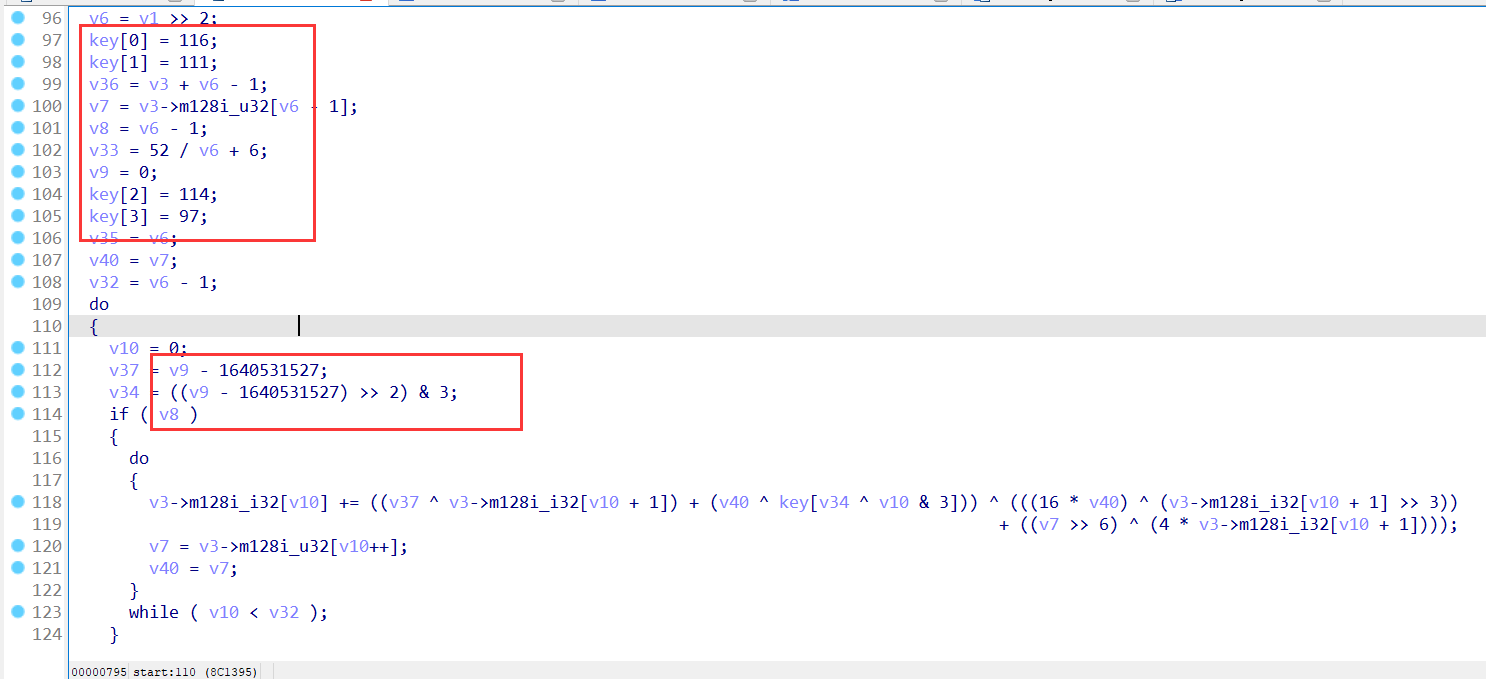
可以看出来是一个xtea加密,密钥和defult都给了出来
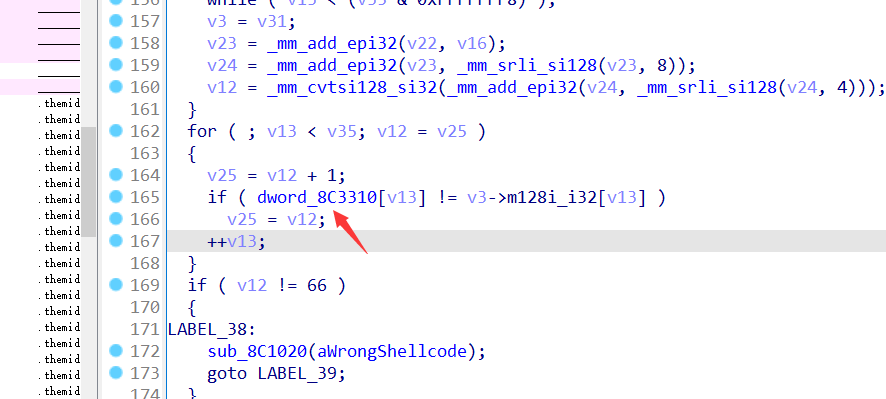
找到对比的位置
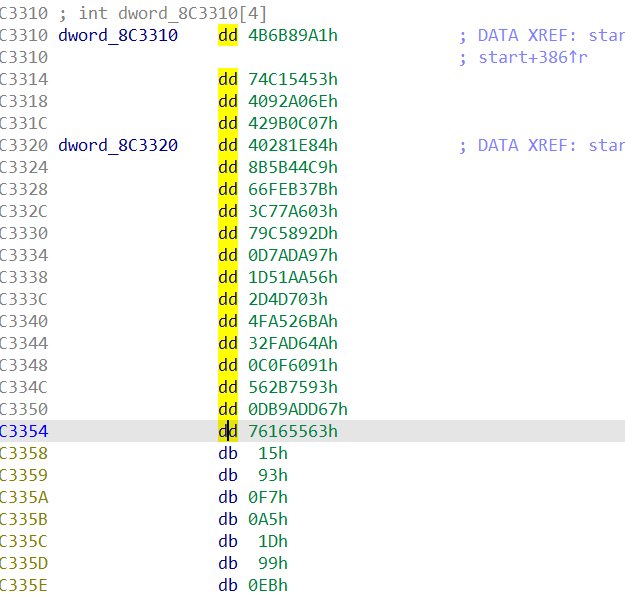
提取需要解密的数据
0x3解密xtea
def ror3(n):
return (n >> 3) | ((n & 7) << 5)
def decrypt(v, key, n):
sum = 0xb54cda56
detal = 0x61C88647
y = v[0]
for k in range(0, 6):
e = (sum >> 2) & 3
for i in range(65, 0, -1):
z = v[i - 1]
v[i] += 0x100000000
v[i] -= ((((z >> 6 ^ (y * 4)) + (y >> 3 ^ (z*16)))
^ ((sum ^ y) + (key[(i & 3) ^ e] ^ z))) & 0xffffffff)
v[i] &= 0xffffffff
y = v[i]
i -= 1
z = v[n-1]
v[0] += 0x100000000
v[0] -= ((((z >> 6 ^ (y * 4)) + (y >> 3 ^ (z*16)))
^ ((sum ^ y) + (key[(i & 3) ^ e] ^ z))) & 0xffffffff)
v[0] &= 0xffffffff
y = v[0]
sum += detal
sum &= 0xffffffff
for i in v:
a1 = i & 0xff
a2 = (i >> 8) & 0xff
a3 = (i >> 16) & 0xff
a4 = (i >> 24) & 0xff
print(hex(ror3(a1)), end = ", ")
print(hex(ror3(a2)), end = ", ")
print(hex(ror3(a3)), end = ", ")
print(hex(ror3(a4)), end = ", ")
if __name__ == "__main__":
# key 初始化
key = [116, 111, 114, 97]
# 从程序中 dump 出的数据
a = [0x4B6B89A1, 0x74C15453, 0x4092A06E, 0x429B0C07, 0x40281E84, 0x8B5B44C9, 0x66FEB37B, 0x3C77A603, 0x79C5892D, 0x0D7ADA97, 0x1D51AA56, 0x02D4D703, 0x4FA526BA, 0x32FAD64A, 0x0C0F6091, 0x562B7593, 0xDB9ADD67, 0x76165563, 0xA5F79315, 0x3AEB991D, 0x1AB721D4, 0xAACD9D2C, 0x825C2B27, 0x76A7761A, 0xB4005F18, 0x117F3763, 0x512CC540, 0xC594A16F, 0xD0E24F8C, 0x9CA3E2E9, 0x0A9CC2D5, 0x4629E61D, 0x637129E3,
0xCA4E8AD7, 0xF5DFAF71, 0x474E68AB, 0x542FBC3A, 0xD6741617, 0xAD0DBBE5, 0x62F7BBE3, 0xC8D68C07, 0x880E950E, 0xF80F25BA, 0x767A264C, 0x9A7CE014, 0x5C8BC9EE, 0x5D9EF7D4, 0xB999ACDE, 0xB2EC8E13, 0xEE68232D, 0x927C5FCE, 0xC9E3A85D, 0xAC74B56B, 0x42B6E712, 0xCD2898DA, 0xFCF11C58, 0xF57075EE, 0x5076E678, 0xD4D66A35, 0x95105AB9, 0x1BB04403, 0xB240B959, 0x7B4E261A, 0x23D129D8, 0xF5E752CD, 0x4EA78F70]
decrypt(a, key, 66)
#0x60, 0xfc, 0x68, 0x4c, 0x77, 0x26, 0x7, 0x33, 0xd2, 0x64, 0x8b,
# 0x52, 0x30, 0x8b, 0x52, 0xc, 0x8b, 0x52, 0x14, 0x8b, 0x72, 0x28,
# 0xf, 0xb7, 0x4a, 0x26, 0x33, 0xff, 0x33, 0xc0, 0xac, 0x3c, 0x61,
# 0x7c, 0x2, 0x2c, 0x20, 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0xe2, 0xf0, 0x52,
# 0x57, 0x8b, 0x52, 0x10, 0x8b, 0x42, 0x3c, 0x3, 0xc2, 0x8b, 0x40, 0x78,
# 0x85, 0xc0, 0xf, 0x84, 0xbe, 0x0, 0x0, 0x0, 0x3, 0xc2, 0x50, 0x8b, 0x48,
# 0x18, 0x8b, 0x58, 0x20, 0x3, 0xda, 0x83, 0xf9, 0x0, 0xf, 0x84, 0xa9, 0x0,
# 0x0, 0x0, 0x49, 0x8b, 0x34, 0x8b, 0x3, 0xf2, 0x33, 0xff, 0x33, 0xc0, 0xac,
# 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0x3a, 0xc4, 0x75, 0xf4, 0x3, 0x7c, 0x24, 0x4, 0x3b,
# 0x7c, 0x24, 0xc, 0x75, 0xd9, 0x33, 0xff, 0x33, 0xc9, 0x83, 0xc2, 0x50, 0xf, 0xb6,
# 0x4, 0xa, 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0x41, 0x83, 0xf9, 0xe, 0x75, 0xf1, 0xc1, 0xcf,
# 0xd, 0x57, 0x33, 0xff, 0x33, 0xc9, 0x8b, 0x54, 0x24, 0x3c, 0x52, 0xf, 0xb6, 0x1c, 0xe,
# 0xb8, 0x67, 0x66, 0x66, 0x66, 0xf7, 0xeb, 0xd1, 0xfa, 0x8b, 0xc2, 0xc1, 0xe8, 0x1f, 0x3,
# 0xc2, 0x8d, 0x4, 0x80, 0x2b, 0xd8, 0x5a, 0xf, 0xb6, 0x4, 0xa, 0x2b, 0xc3, 0xc1, 0xcf, 0xd,
# 0x3, 0xf8, 0x41, 0x83, 0xf9, 0xe, 0x75, 0xd4, 0xc1, 0xcf, 0xd, 0x3b, 0x3c, 0x24, 0x74, 0x16,
# 0x68, 0x25, 0x73, 0x0, 0x0, 0x8b, 0xc4, 0x68, 0x6e, 0x6f, 0x0, 0x0, 0x54, 0x50, 0x8b, 0x5c, 0x24,
# 0x48, 0xff, 0xd3, 0xeb, 0x14, 0x68, 0x25, 0x73, 0x0, 0x0, 0x8b, 0xc4, 0x68, 0x79, 0x65, 0x73, 0x0,
# 0x54, 0x50, 0x8b, 0x5c, 0x24, 0x48, 0xff, 0xd3, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58,
# 0x61, 0xc3, 0x58, 0x5f, 0x5a, 0x8b, 0x12, 0xe9, 0xb, 0xff, 0xff, 0xff再进行一个base64加密
import base64
a=[0x60, 0xfc, 0x68, 0x4c, 0x77, 0x26, 0x7, 0x33, 0xd2, 0x64, 0x8b, 0x52, 0x30, 0x8b, 0x52, 0xc, 0x8b, 0x52, 0x14, 0x8b, 0x72, 0x28, 0xf, 0xb7, 0x4a, 0x26, 0x33, 0xff, 0x33, 0xc0, 0xac, 0x3c, 0x61, 0x7c, 0x2, 0x2c, 0x20, 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0xe2, 0xf0, 0x52, 0x57, 0x8b, 0x52, 0x10, 0x8b, 0x42, 0x3c, 0x3, 0xc2, 0x8b, 0x40, 0x78, 0x85, 0xc0, 0xf, 0x84, 0xbe, 0x0, 0x0, 0x0, 0x3, 0xc2, 0x50, 0x8b, 0x48, 0x18, 0x8b, 0x58, 0x20, 0x3, 0xda, 0x83, 0xf9, 0x0, 0xf, 0x84, 0xa9, 0x0, 0x0, 0x0, 0x49, 0x8b, 0x34, 0x8b, 0x3, 0xf2, 0x33, 0xff, 0x33, 0xc0, 0xac, 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0x3a, 0xc4, 0x75, 0xf4, 0x3, 0x7c, 0x24, 0x4, 0x3b, 0x7c, 0x24, 0xc, 0x75, 0xd9, 0x33, 0xff, 0x33, 0xc9, 0x83, 0xc2, 0x50, 0xf, 0xb6, 0x4, 0xa, 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0x41, 0x83, 0xf9, 0xe, 0x75, 0xf1, 0xc1, 0xcf, 0xd, 0x57, 0x33, 0xff, 0x33, 0xc9, 0x8b, 0x54, 0x24, 0x3c, 0x52, 0xf, 0xb6, 0x1c, 0xe, 0xb8, 0x67, 0x66, 0x66, 0x66, 0xf7, 0xeb, 0xd1, 0xfa, 0x8b, 0xc2, 0xc1, 0xe8, 0x1f, 0x3, 0xc2, 0x8d, 0x4, 0x80, 0x2b, 0xd8, 0x5a, 0xf, 0xb6, 0x4, 0xa, 0x2b, 0xc3, 0xc1, 0xcf, 0xd, 0x3, 0xf8, 0x41, 0x83, 0xf9, 0xe, 0x75, 0xd4, 0xc1, 0xcf, 0xd, 0x3b, 0x3c, 0x24, 0x74, 0x16, 0x68, 0x25, 0x73, 0x0, 0x0, 0x8b, 0xc4, 0x68, 0x6e, 0x6f, 0x0, 0x0, 0x54, 0x50, 0x8b, 0x5c, 0x24, 0x48, 0xff, 0xd3, 0xeb, 0x14, 0x68, 0x25, 0x73, 0x0, 0x0, 0x8b, 0xc4, 0x68, 0x79, 0x65, 0x73, 0x0, 0x54, 0x50, 0x8b, 0x5c, 0x24, 0x48, 0xff, 0xd3, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x58, 0x61, 0xc3, 0x58, 0x5f, 0x5a, 0x8b, 0x12, 0xe9, 0xb, 0xff, 0xff, 0xff]
flag =b''
for i in a:
flag +=i.to_bytes(1,'big')
b=base64.b64encode(flag)
print(b)
#YPxoTHcmBzPSZItSMItSDItSFItyKA+3SiYz/zPArDxhfAIsIMHPDQP44vBSV4tSEItCPAPCi0B4hcAPhL4AAAADwlCLSBiLWCAD2oP5AA+EqQAAAEmLNIsD8jP/M8Cswc8NA/g6xHX0A3wkBDt8JAx12TP/M8mDwlAPtgQKwc8NA/hBg/kOdfHBzw1XM/8zyYtUJDxSD7YcDrhnZmZm9+vR+ovCwegfA8KNBIAr2FoPtgQKK8PBzw0D+EGD+Q511MHPDTs8JHQWaCVzAACLxGhubwAAVFCLXCRI/9PrFGglcwAAi8RoeWVzAFRQi1wkSP/TWFhYWFhYWFhYYcNYX1qLEukL////
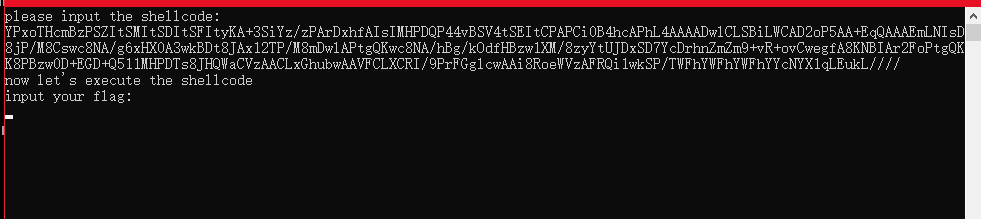
0x4 分析第二个flag输入
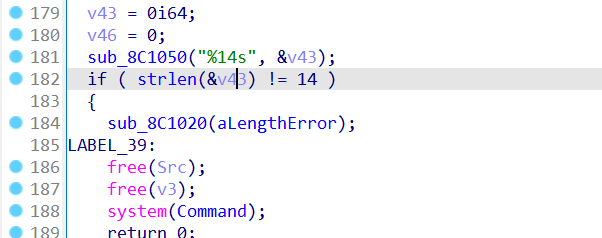
要求输入14位
0x5 动调开始了
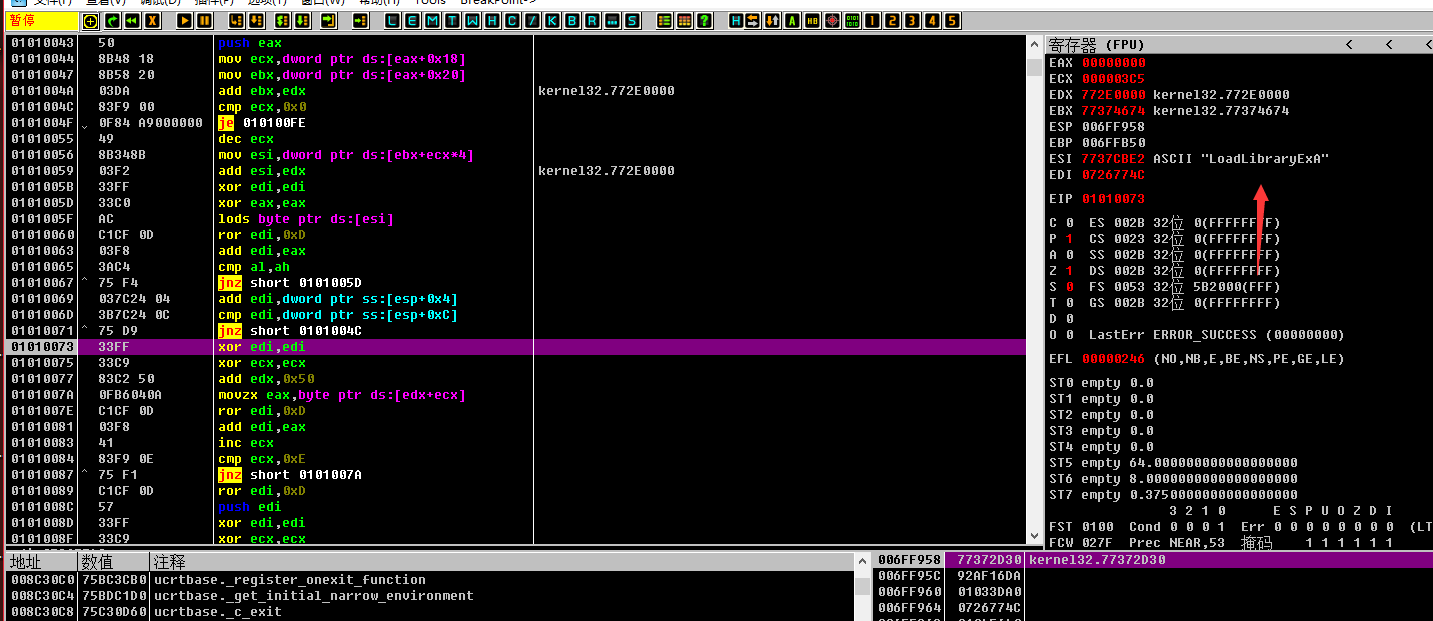
可以看见最终寻找了这个字符串
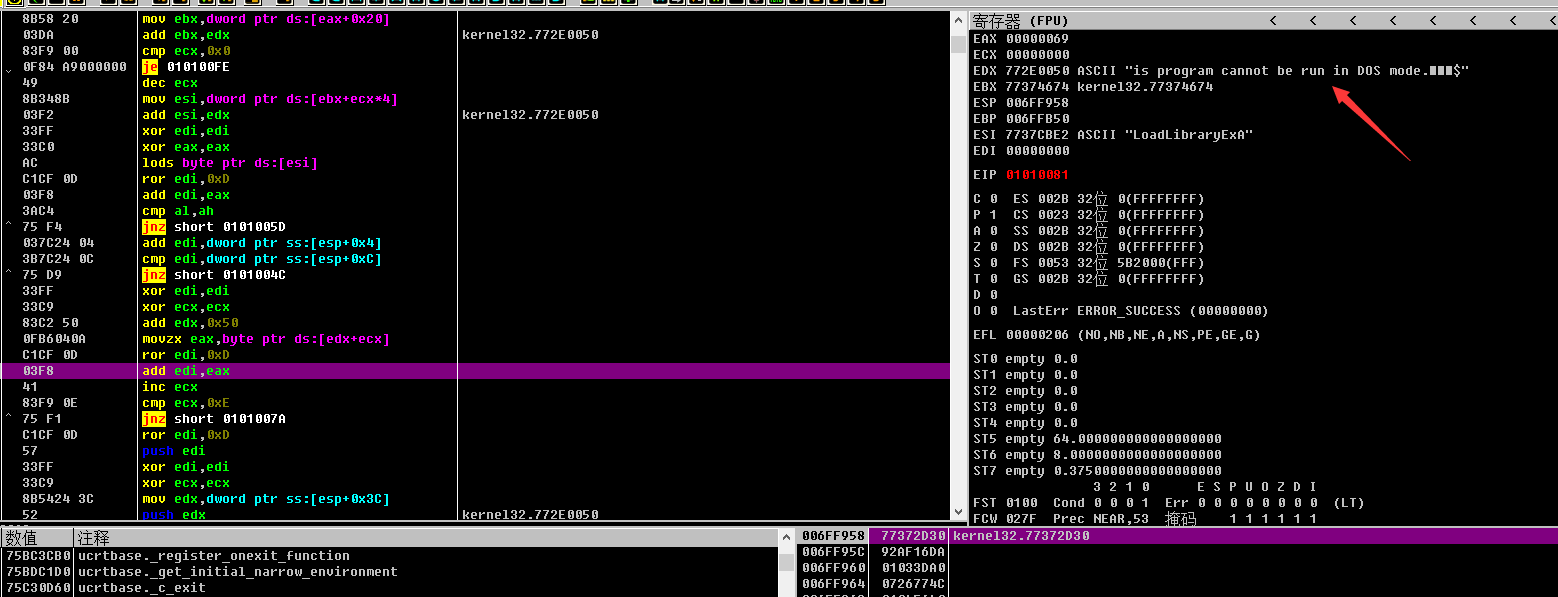
然后找到了这一串字符串
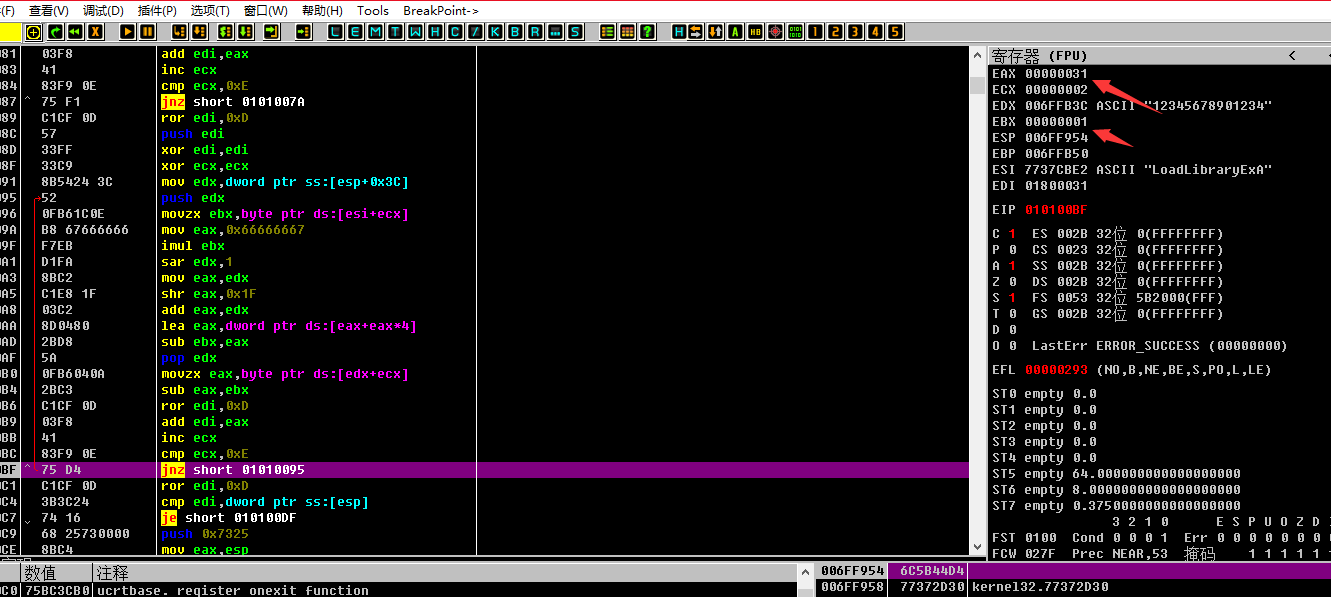
再用第二个字符取出14个每次减一个0-4的值,动调提取出来。(实际上是第二个字符串减去第一个字符串%5)在od里展现出来就是每次减一个0-4的值了
0x6 解密第二个字符串加减
k = [1,1,2,0,1,0,3,4,2,4,1,4,0,0]
a = 'is program can'
for i in range(len(k)):
print(chr(ord(a[i])+k[i]),end='')
#jt"psojvcq!gan0x7 成功!!
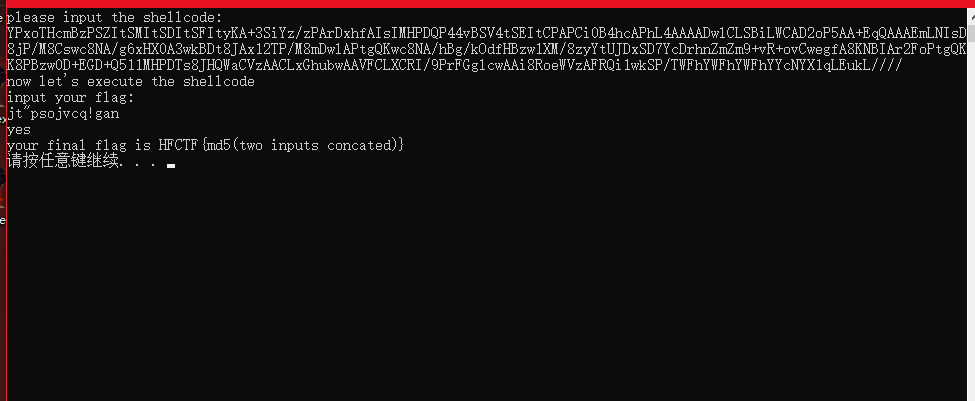
0x8 总结
原本不想写的,但是今天投简历,发现个人博客也是一个很好的发光点,只好努力丰富一下了,说不定找工作就用上了。
感谢一下战队里的emtanling师傅,看了他的博客和讲解,非常感谢。下面贴他博客!!



