2022HWS-REVER
RE1
0x1 静态分析
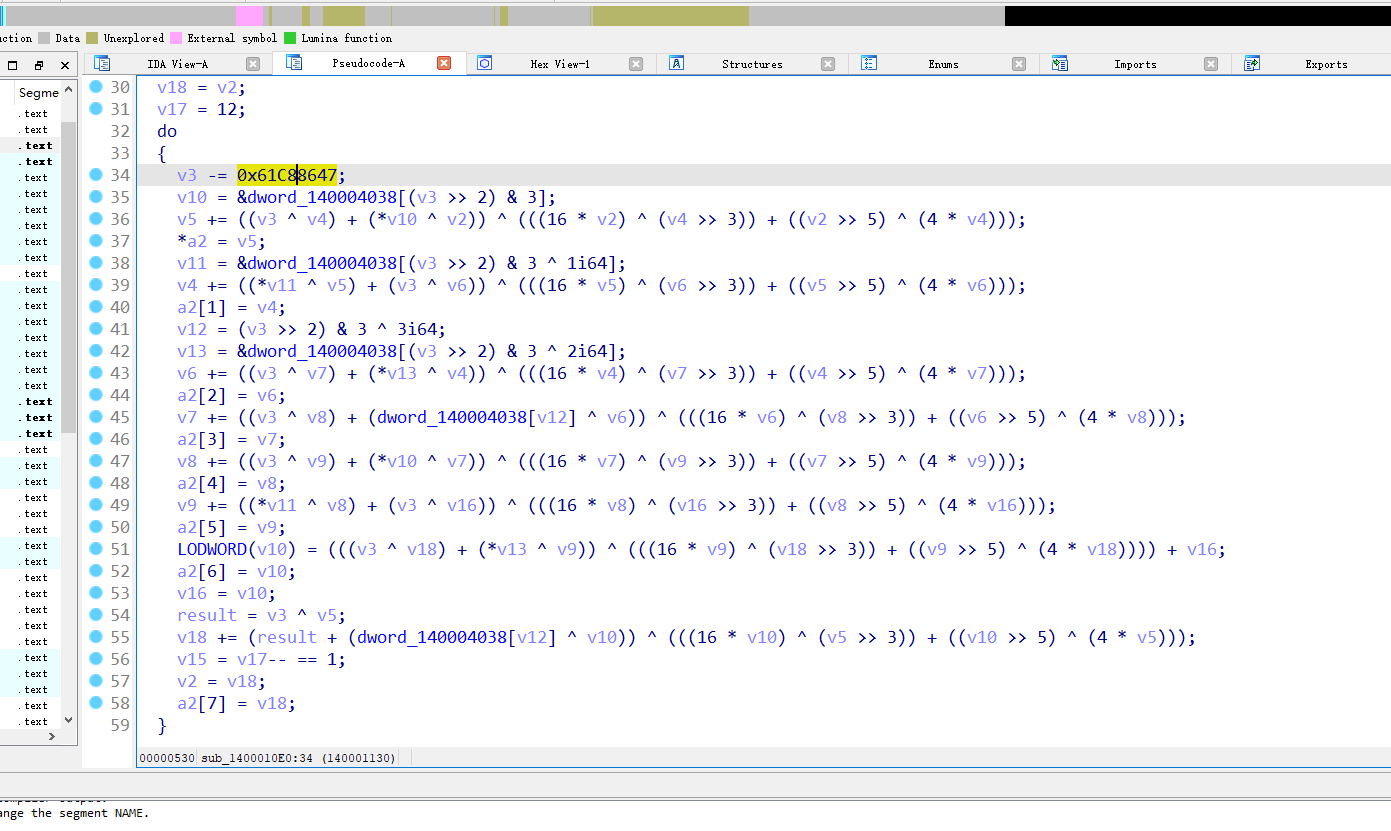
xxtea加密无魔改
0x2 解密
#include <stdio.h>
#include <stdint.h>
#include <windows.h>
#define DELTA 0x9E3779B9
#define MX (((z>> 5^y<< 2) + (y>> 3^z<< 4)) ^ ((sum^y) + (key[(p&3)^e] ^z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1)
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum > 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1)
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p --)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
int main() {
uint32_t const key[4] = { 0x1234, 0x2345, 0x4567, 0x6789 };
uint32_t v[] = {0x10BD3B47, 0x6155E0F9, 0x6AF7EBC5, 0x8D23435F, 0x1A091605, 0xD43D40EF, 0xB4B16A67, 0x6B3578A9 };
btea(v, -8, key);
unsigned char * p = (unsigned char *)v;
for (int i = 0; i < 8; i++)
{
for (int j = 0; j < 4; j++)
{
printf("%c", p[i*4+j]);
}
}
return 0;
}flag{7f943921724d63dc0ac9c6febf99fa88}
RE2
0x0 前言
这题就有意思了,出题人我认识,发给当事人说是去年年初出的,笑死我了
0x1 分析
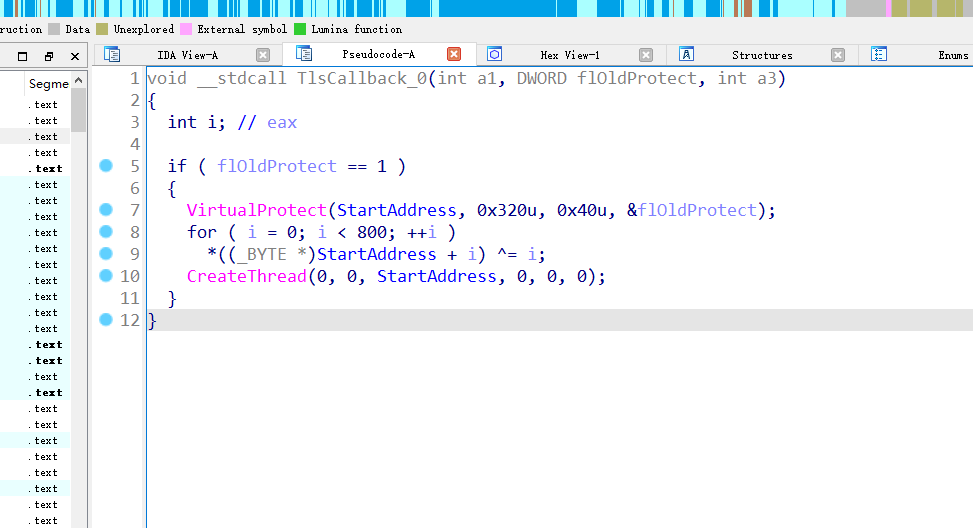
tlsCALLback,直接动调起来看
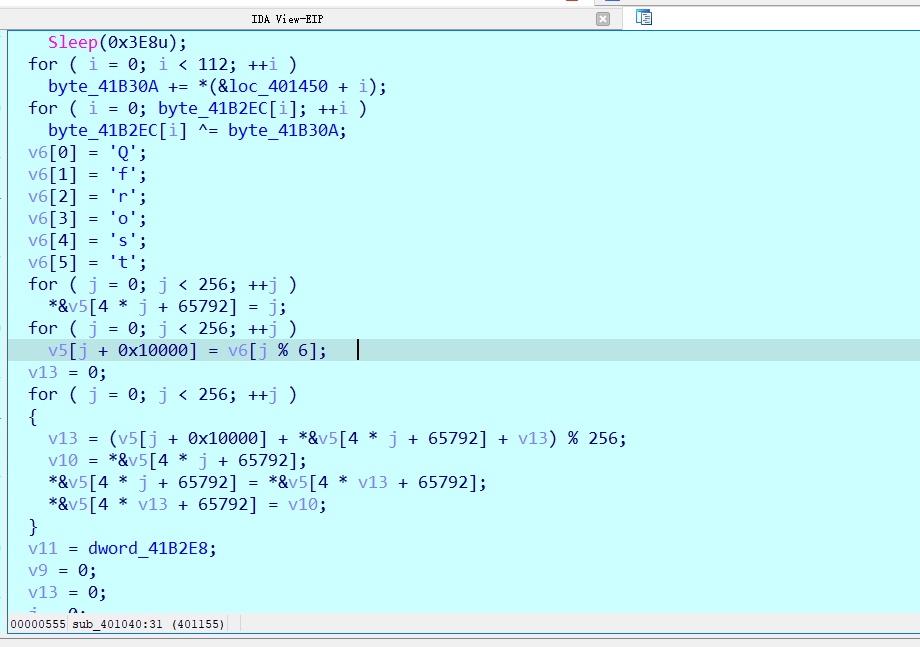
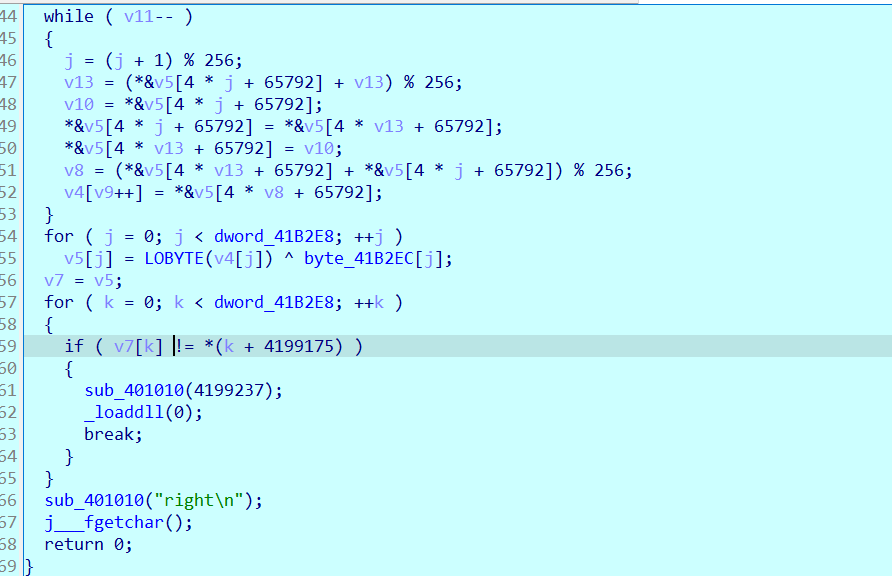
最开始有一个异或,我直接改eip到加密位置跑,看见是0x48
然后就是rc4 key都给了 ,再把密文dump一下ok了
0x2 解密
from Crypto.Cipher import ARC4 as rc4cipher
a = [0x7F, 0xB6, 0x88, 0x12, 0xDC, 0xC3, 0xDE, 0xDB,0x30]
b=b""
for i in range(len(a)):
b+=chr(a[i]).encode("utf-8")
key = b'Qfrost'
enc = rc4cipher.new(key)
res = enc.decrypt(b)
print(res)
for i in range(len(res)):
print(res[i]^0x48)a=[0x46, 0x40, 0x49, 0x46, 0x7F, 0x52, 0x6E, 0x46, 0x7C, 0x24,
0x6B, 0x26, 0x5C, 0x64, 0x7A, 0x5B, 0x49, 0x6C]
b=0x48
c=[0x7F, 0xB6, 0x88, 0x12, 0xDC, 0xC3, 0xDE, 0xDB,0x30]
d=[0x19
,0xc
,0x2a
,0x2f
,0x65
,0x1
,0x3b
,0x17
,0x29
,0x26
,0x17
,0x79
,0x26
,0x3c
,0x2d
,0x3a
,0x2d
,0x1b
,0x3c
,0x21
,0x26
,0x2f
,0x65
,0xf
,0x29
,0x25
,0x2d
,0x69]
flag =""
for i in range(28):
flag +=chr(d[i]^0x48)
print(flag)
# QDbg-Is_an_1ntereSting-Game!RE3
0x1 静态分析
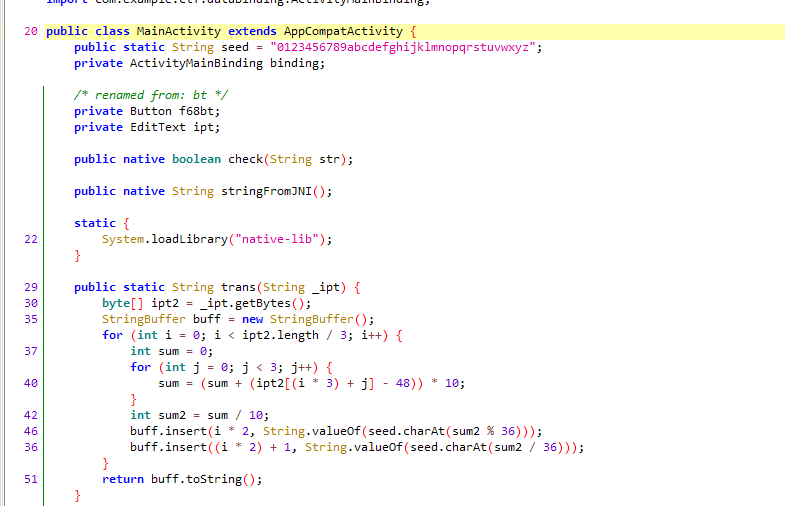
java层一个 base36转换
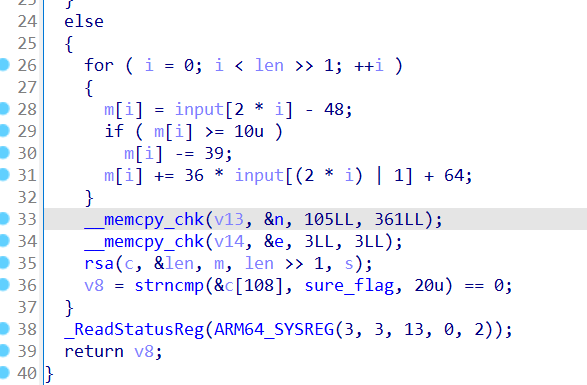
so层一个 36进制转16进制,然后进行rsa加密,n和e都给了要求最终对比开头的一个字符串
import binascii
import gmpy2
n=3210376012670931761316502170991203951906804638852723544409910738462486003580720382031642493934395058562016412694207017986129830212764225207907691741712702720674161648798881029225312212293002061162615582140975099114354997130902078528039351463600638487687
p=1475203612633975218848450285487339190962027688336790188873776418606441616307026173067
q=1475203612633975218848450285487339190962027688336790188873776418606441616307046219549
r=1475203612633975218848450285487339190962027688336790188873776418606441616307129708089
e=65537
c=0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000004920616d207375726520697420697320666c3467
N=p*q*r
phi=(p-1)*(q-1)*(r-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,N)
print(hex(m))
print(binascii.unhexlify(hex(m)[2:].strip("L")))
# a=0x876cc53c98eb249561a0bd232c349c505dd27ff7cc3da537ecff45e1759d7c824885294aa5f7acab86065cdabfe29f3a6ec3aceb43a8a147744c8475e7b2cc2146effab85ddba90dd308660d6239decd45c53ebca15e46d20a0211926ef2a2f4705b321970
# b=903015085039400505825173703410270086306776880410650467917599965981213376560196802316787937322039493430010084087983817206119395110985353714317144118472450426801108638990191292853919023158451032156229083706845999330492119033537079097510648224112
# import gmpy2
#
# msg = 'I am sure it is fl4g1'
# msg_hex=0x396e2be87db2cafc5805f0963696c5209a53ca3c73f0dffdcf74a779f602405c0700edcfbedd94b529bebc7a3d0d549b372dcd29f29741e28ee57cea3c2c0a347b13315bf135b6170fe3a13c013925f7db29db98076f3ff6f7ed7ce828637e9d9200858939d2a7aec5
# p=1475203612633975218848450285487339190962027688336790188873776418606441616307026173067
# q=1475203612633975218848450285487339190962027688336790188873776418606441616307046219549
# r=1475203612633975218848450285487339190962027688336790188873776418606441616307129708089
# n=p*q*r
# e=0x10001
# phi=(p-1)*(q-1)*(r-1)
# d=gmpy2.invert(e,phi)
# print("d=",hex(d))
# c=pow(msg_hex,e,n)
# print("e=",hex(e))
# print("n=",hex(n))
# print("c=",hex(c))
rsa解密,我同时构造了一下格式
import base64
base = [0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37, 0x38, 0x39, 0x61, 0x62, 0x63, 0x64, 0x65, 0x66, 0x67, 0x68, 0x69, 0x6a, 0x6b, 0x6c,
0x6d, 0x6e, 0x6f, 0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78, 0x79, 0x7a]
data="11d7ef63b4dra1a3cnakddk0d9d292fnemegg7e8ea72bnd8g9cmcjd1akako3gdn1f2c3fgaea0eof3d993aha0c1f862eoffe15261ele2gidogrba90bna933l1j1o070ef70j0baeeb9n0g941l1cmcddndgh2acan4313h0l3fp3062k2a8f9bkc983d9aia121gnaeblglcd"
for i in range(0,len(data),2):
print(str(data[i:i+2]),end=",")
print()
data=[0x25,0x57,0x83,0xdb,0x0c,0x6b,0xe5,0xe7,0x43,0xf8,0x5d,0x4c,0x59,0x52,0x46,0xaf,0x8a,0x84,0xc3,0x7c,0x7e,0xfe,0x1f,0x58,0xc5,0x42,0x3f,0x51,0xf8,0xf8,0xdf,0xc9,0xb9,0x9a,0x2f,0xa8,0xf2,0xe4,0x8c,0x9b,0x59,0x47,0xf5,0xe4,0x2d,0xa0,0xda,0x8c,0xa7,0x75,0xb6,0xd9,0x89,0x76,0xce,0x68,0xd7,0x12,0x44,0x1f,0xed,0x6f,0x71,0x29,0xdc,0xfc,0x83,0xfc,0x28,0x12,0x82,0x11,0xb8,0xc5,0x91,0x71,0x42,0x39,0x67,0x60,0xe2,0xf0,0xfb,0x93,0x27,0xe0,0x73,0xb1,0x6c,0xda,0x4e,0xec,0xa1,0x1c,0x35,0x23,0x59,0xf6,0xe5,0x49,0xd3,0xf2,0x1d,0xd1,0x39]
for i in range(len(data)-1,-1,-1):
print(hex(data[i]),end=",")
print()
for i in range(len(data)):
for j in range(32):
v8 = base[j] - 48
if v8 > 10:
v8 -= 39
v9 = v8
for k in range(32):
v8 += 36 * base[k] + 64
if v8 & 0xff == 0x57:
print(chr(base[j]), end=",")
print(chr(base[k]), end=",")
break
else:
v8 = v9
print()
a=["11","d7","ef","63","b4","dr","a1","a3","cn","ak","dd","k0","d9","d2","92","fn","em","eg","g7","e8","ea","72","bn","d8","g9","cm","cj","d1","ak","ak","o3","gd","n1","f2","c3","fg","ae","a0","eo","f3","d9","93","ah","a0","c1","f8","62","eo","ff","e1","52","61","el","e2","gi","do","gr","ba","90","bn","a9","33","l1","j1","o0","70","ef","70","j0","ba","ee","b9","n0","g9","41","l1","cm","cd","dn","dg","h2","ac","an","43","13","h0","l3","fp","30","62","k2","a8","f9","bk","c9","83","d9","ai","a1","21","gn","ae","bl","gl","cd"]
# for i in range(len(a)):
# print(a[i][1],end="")
# print(a[i][0],end="")
for i in range(len(a)):
if int(a[i],36) < 100:
print("0",end="")
print(int(a[i],36),end="")
continue
print(int(a[i], 36),end="")
print()
b="037374755192194004953613634553804817204774703265635265205835125142544194765854544514693803808675898295424355563743605285434773273773604335482185285555051822175255065944926034063244193691117576858642525192526844065184058285851457574544454914846143723831470393961275956510821872236854941644129147737836107373599374417597445"
print(len(b))解出来rsa分割成0xff的格式 因为有最开始的base36转换所以我就直接爆破了
然后一定要记得改变爆破出来的左右顺序,然后改成10进制不足3位补0
总结
学到了很多,尤其是第三题,太多没看出实际操作了,还好百度一直搜到了



